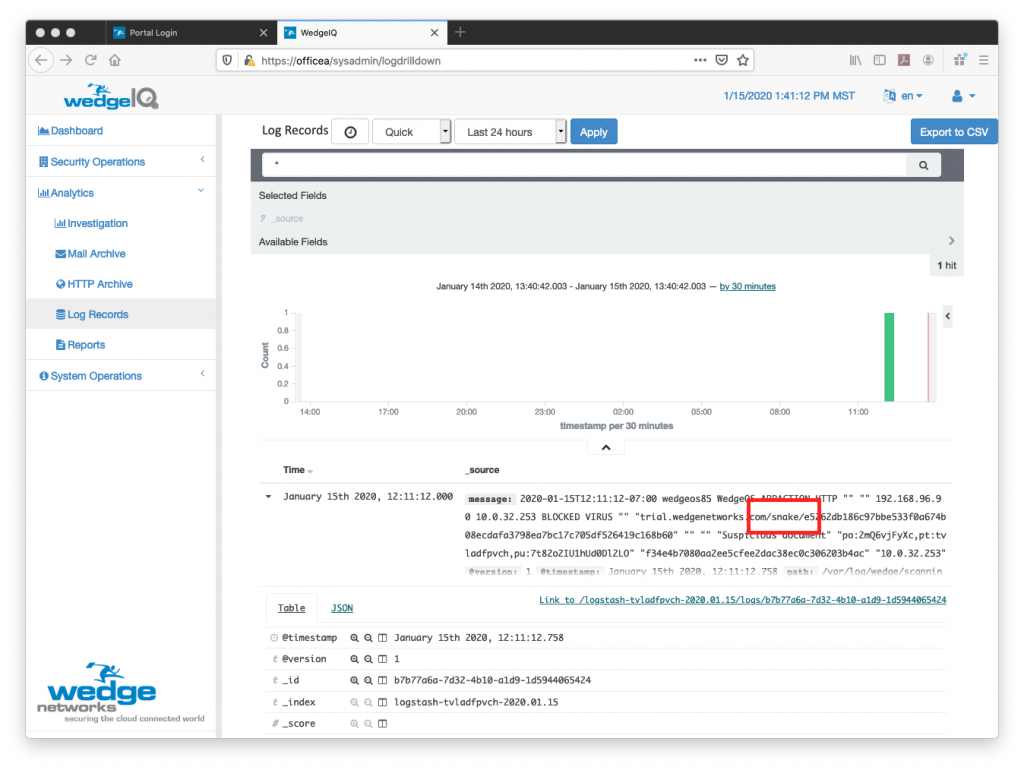
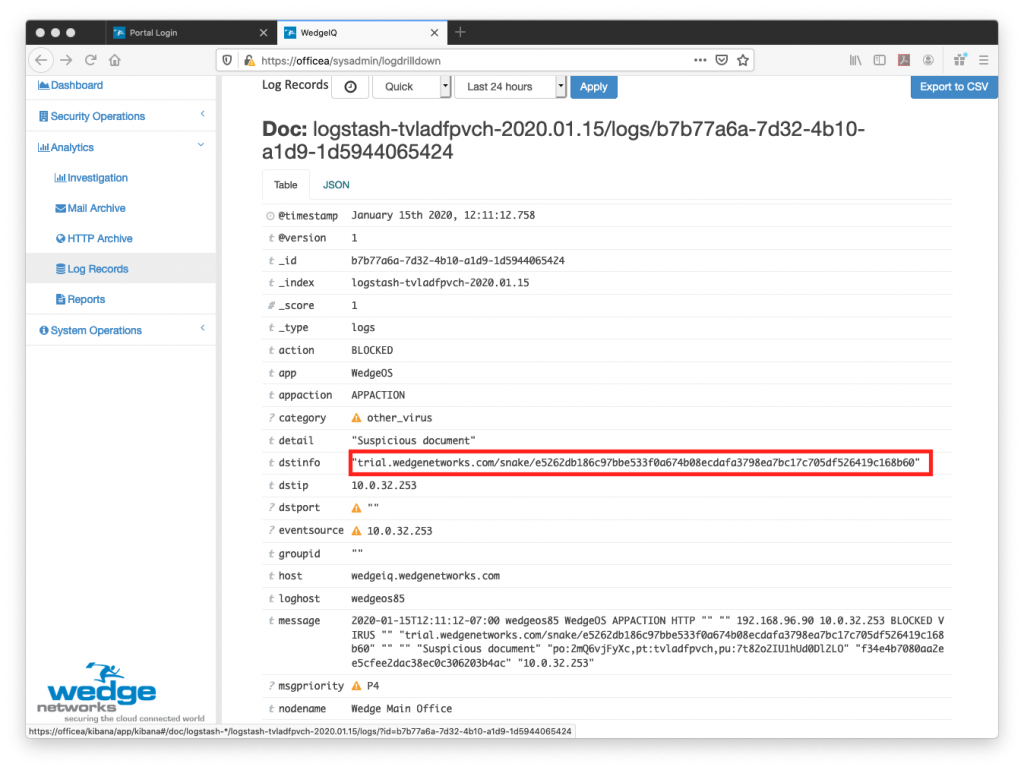
This is a follow-up blog to the one we provided earlier this month on how the Snake Ransomware was affecting Corporate Networks.
Yesterday, Bloomberg again brought to light the recent “Snake” ransomware and how it is now used to target Industrial Control Systems (ICS); and in particular, many industrial processes that belong to General Electric Co. This new strain of ransomware was created by Iran and has the ability to lock up and even delete ICSs. Snake will encrypt programs and documents on infected machines BUT it also removes all file copies from infected stations, preventing victims from even recovering encrypted files. As such, deleting and/or locking targeted ICS processes would prevent manufacturers from accessing vital production-related processes such as analytics, configuration and control.
Of note, before the Snake ransomware starts encrypting files, it attempts to terminate processes associated with various types of programs, including system utilities, enterprise management tools and ICS. Although other companies such as Honeywell and their processes are at risk, the majority of the industrial processes that are targeted by Snake are those in GE products.
According to an article by SecurityWeek, one organization that was recently targeted by this ransomware (or the related Dustman malware) was the Bahrain Petroleum Company (Bapco). According to ZDNet Saudi officials sent an alert to other local companies active on the energy market in an attempt to warn of potential attacks and advising these companies to ensure that their networks were secure. The Bapco incident was brought up amid rising tensions between the US and Iran after the US military recently killed top Iranian military general, Major General Qassim Suleimani.
Saudi Arabia’s National Cybersecurity Authority subsequently linked Dustman to the ZeroCleare malware; itself a wiper that has been targeted against energy and industrial organizations in the Middle East. When the dust settles, all of these malware variations have been linked back to Iranian hacker groups, and are a testament to Iran’s advanced technical capabilities when it comes to launching destructive state-endorsed cyber attacks. With the current political climate surrounding Iran and the US, it would not be prudent to rule out the possibility that they will try to create additional instability by targeting other energy and industrial / infrastructure organizations in the region.
That being said, if your organization is running any sort of ICS system that could potentially be at risk, how confident are you in the security solutions that you currently have in place? How damaging would a ransomware attack be to your organization? Are you prepared with backup plans? In this case, should the Snake ransomware hit your operations, because it removes all file copies from infected stations, would paying the ransom even ensure that you’ll be able to get up and running again?
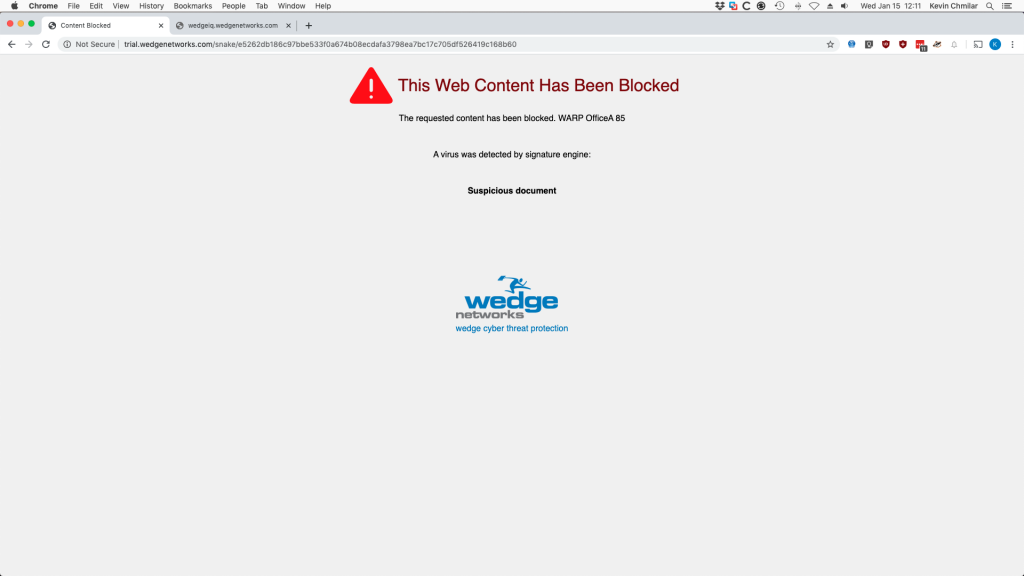
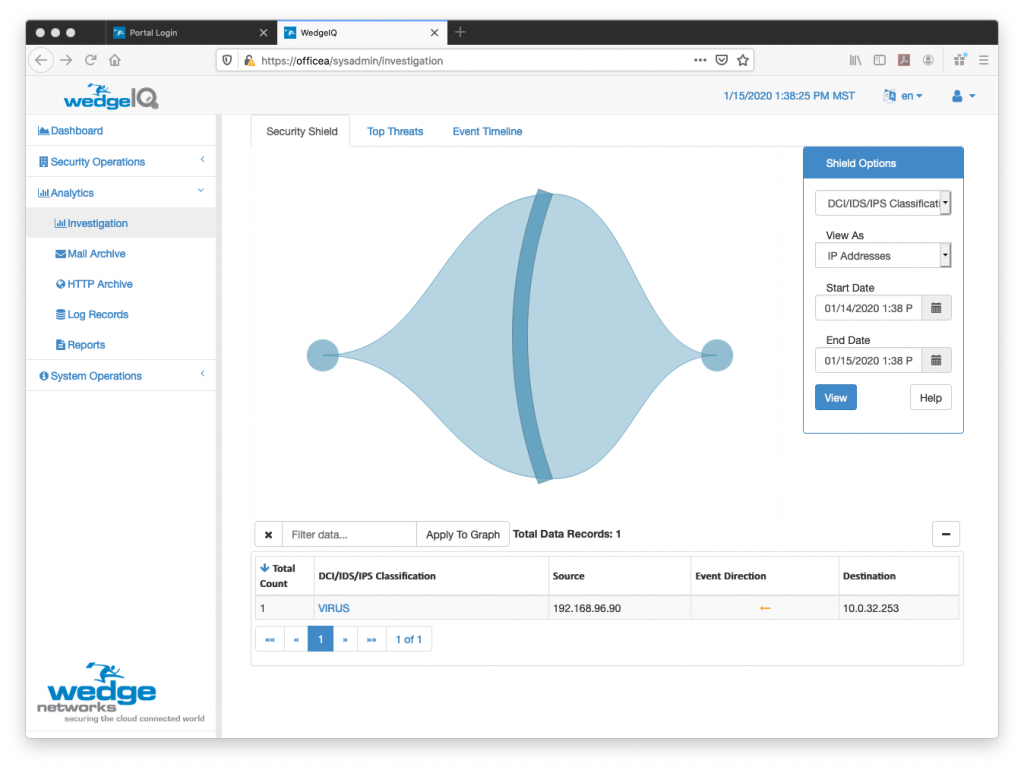
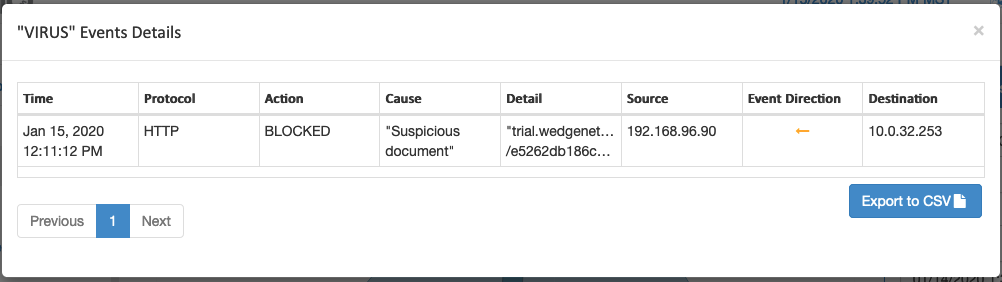
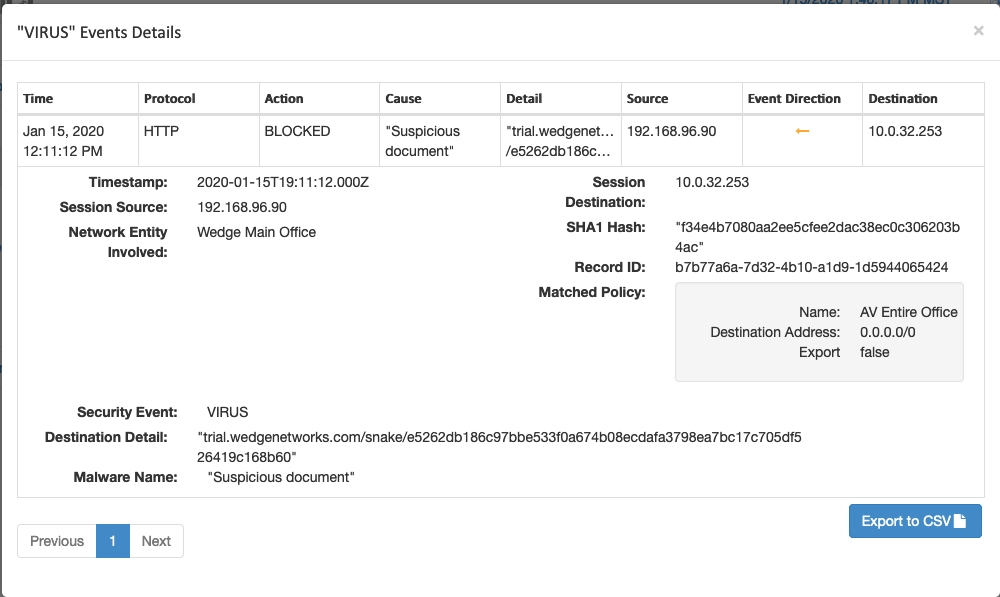
This is where Wedge, and its ability to detect the Snake ransomware, is able to help. With Wedge’s Advanced Malware Blocker (WedgeAMB) in place, the Snake malware that is targeting ICSs can easily be detected and blocked in real-time, BEFORE it causes any damage. With a deep content inspection, and AI / Machine-learning based platform that has proven effective to be able to detect and block ransomware in real-time, WedgeAMB is providing not only Energy and Industrial organizations but ALL organizations the extra blanket of protection that they need to weather the new variations of ransomware that are being pushed out by hacker organizations.
If your organization is concerned about this recent spate of attacks, and is unsure of whether your security solution would be able to detect the Snake ransomware, make sure to contact us at: info@wedgenetworks.com. Our team will be able to tell you more about how WedgeAMB can protect your organization. WedgeAMB is available for a FREE 90 day trial so you really have nothing to lose!