I have been away for a much needed holiday, spending quality time with my in-laws. Apart from the typical gastronomical splurging (what else – Swiss chocolates, Swiss Cheese, etc.), holidays are a good time to reflect.
Trains and Europe go hand in hand and while waiting for my train at Zurich HB Station, I noticed how simple, elegant and impeccably accurate all the stations’ clocks were. Later that night, I read all about this timeless clock. Designed by Hans Hilfiker in the 40s, this simple, elegant and impeccably accurate design is timeless and goes to prove that most problems require just that – simple, elegant, yet impecabbly accurate solutions.
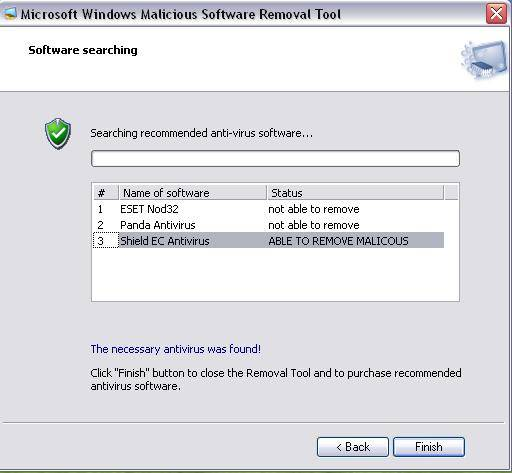
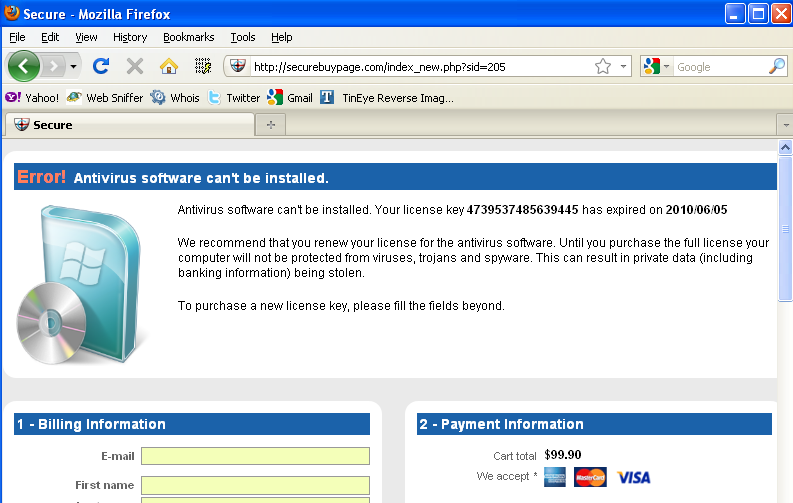
Thinking of our industry – providing security to computer networks and end-devices, I am not sure we are at that stage yet. Here is why:
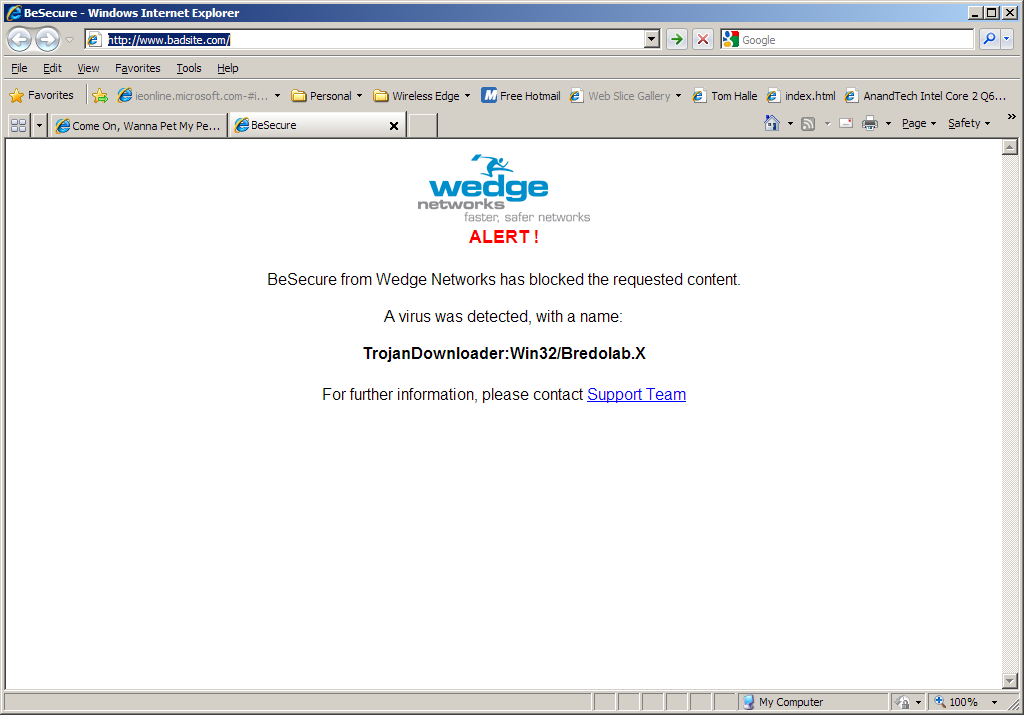
The Ponemon Institute reports that (See bar chart 3 of the report) enterprises, on average, have 3.7 software agents installed on each endpoint to perform management, security and other operations. In addition, these enterprises have, on average, 3.9 different or distinct software management consoles for endpoint operations and security. Yet, (See bar chart 17 of the report), more than 88% of these enterprises reported that virus or malware network intrusions were the most frequently encountered incidents experienced in 2008/2009!
Ponemon reports that enterprises have 3.7 software agents installed on each endpoint to perform management, security and other operations, yet 88% of these enterprises reported that virus or malware network intrusions were the most frequently encountered incidents.
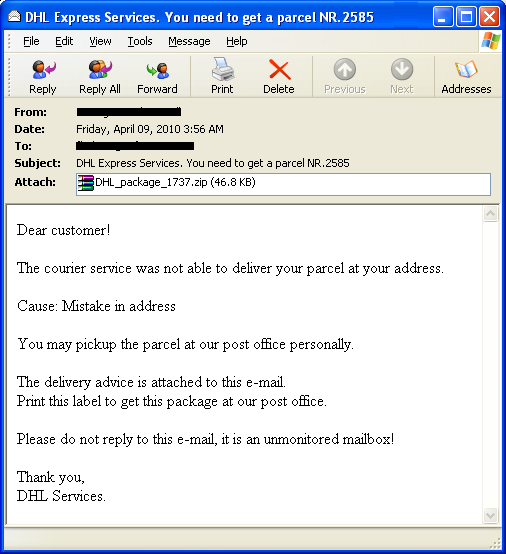
And further, the daily headlines continue to prove that we need to change our approach. The latest, Yet-Another-Adobe-Exploit (YAAE!), utilizes an old-school download and run approach – VBMania worm. The worm propagates itself by sending you an e-mail with the title “Here you have” as shown:
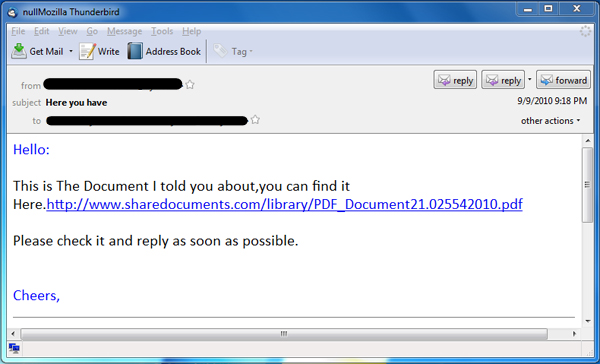
"Here you have" VBMania Worm Infected Message
While the document has been removed, hence, in effect, this worm has been killed, this simple PDF exploit goes to prove this: With all the complex endpoint solutions, or UTMs that we have installed, out there, we need simple, elegant yet accurate security solutions. In the followup blogs, I will further elaborate on what this entails.