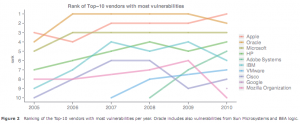
The new iPhone 4.0 is a piece of art, a handheld device which Andrew Berg of Wireless Week elegantly termed as ‘beautifuly flawed‘. Surprisingly, another report that went out un-noticed by mainstream media, unless you are in the Security business, rated Apple as the company with the most security vulnerabilities in its software, surpassing Oracle and even Microsoft in the last 5 years. This is shown by the now highly quoted, yet highly disputed, graph:
But it is not just the iPhone or Apple platforms that are going to see a surge in malware attacks due to these documented vulnerabilities. Kaspersky made this critical prediction in December 2009:
An increase in attacks on iPhone and Android mobile platforms. 2010 promises to be a difficult time for iPhone and Android users. The first malicious programs for these mobile platforms appeared in 2009, a sure sign that they have aroused the interest of cybercriminals. The only iPhone users currently at risk are those with compromised devices; however the same is not true for Android users who are all vulnerable to attack. The increasing popularity of mobile phones running the Android OS combined with a lack of effective checks to ensure third-party software applications are secure, will lead to a number of high-profile malware outbreaks.
There are three reasons why this prediction will hold and mobile devices are the next target for malicious attacks. First, newer, more accessible platforms and applications – and the vulnerabilities highlighted above – will open the doors to malicious attacks on and from mobile devices. And second, many of us are using our iPhones and Android Smartphones in the same way we use our PCs. We shop, surf the web, email, text, Twitter, Facebook and download on our phones. Thirdly, our phones house so much of our personal information – contacts, calendars, emails, texts, pictures and more – making them a valuable target for malware writers and malicious hackers.
So if you are the Chief Security Officer for your Enterprise or Service Provider, mobile devices are at your network’s perimeter and you will need to consider “edge” security solutions (which are typically transparent inline network traffic scanning solutions) – solutions that will protect your end-users’ mobile devices from malware attacks, and in so doing protecting your network infrastructure from attacks launched from compromised mobile devices.
You heard it here first – it is not just the antenna.



Pingback: Tweets that mention And it is not just the antenna… | -- Topsy.com
This security vulnerability becomes more evident with the ability to Jailbreak your iPhone by simply visiting the website http://www.jailbreakme.com. Without even requiring a separate computer, iPhone users are now able to browse to the website with their built-in Safari browsers on their phone, swipe across the screen and an embedded program on the website will download itself to the phone and jailbreak it within minutes (granted as long as the website doesn’t go down because of the vast numbers of people visiting it).
Even if the website were to go down, the alternate method of jailbreaking your iPhone would be to e-mail to your phone a specific pdf file (different pdf files have been customized to take into account whether your iPhone is a 3G, 3GS or 4 flavour running OS 3.1.2 to 4.0.1 – this works for the iPad and iPod Touch too by the way) and then open up the pdf file in the e-mail. This method uses a pdf exploit to download and render the pdf file, injecting the jailbreak payload; essentially going into the phone and allowing the hack to take place.
And here comes a major dilemma… for those that are security conscious, do you willingly allow this program to hack into your iPhone, potentially making your valuable information readily accessible to hackers/malware writers, just so that you have access to the functionalities that come with having a jailbroken phone? It seems that millions of iPhone, iPod Touch and iPad users are willing to go through this process… but at what security cost? And how about ‘fake’ jailbreaking applications? The point remains – there is a need to be browsing through some gateway that has the ability to do a deep content inspection.
Pingback: Come on Kiddo, Wanna pet my pet hamster? |
ohhh nice info
Love your site man keep up the good work
As a Newbie, I am always searching online for articles that can help me. Thank you
This is such a great resource that you are providing and you give it away for free. I enjoy seeing websites that understand the value of providing a prime resource for free. I truly loved reading your post. Thanks!
Hello Guru, what entice you to post an article. This article was extremely interesting, especially since I was searching for thoughts on this subject last Thursday.
Pretty nice post. I just stumbled upon your blog and wished to say that I’ve truly enjoyed browsing your blog posts. After all I’ll be subscribing to your rss feed and I hope you write again very soon!
I was looking for this the other day. i dont usually post in forums but i wanted to say thank you!
Pingback: Gregory Smith