
The Issue:
In an article published on ZDNet, author Liam Tung described a malicious campaign that uses file-naming trickery to get victims to download the key logger Snake malware. Once infected, keystrokes such as entering online banking information are recorded and leaked to cyber criminals.

The Cause:
The Snake keylogger initially appeared in 2020 and has been resurfacing with new variants ever since. It is commonly bundled in a compromised Excel file, PDF, or Word document. A macro code within the compromised document downloads the malware payload from an external server, at which point the malware executes and begins recording user keystrokes and sensitive data. Snake keyloggers are used to particularly target businesses and its effects are widespread.
In this malicious campaign, cyber criminals sent emails with an attached PDF document named “REMMITANCE INVOICE.pdf” with an embedded Word document named “has been verified. However PDF, Jpeg, xlsx, .docs”. When clicked, this odd Word file name is combined with the typical Adobe reader message and reads “The file ‘has been verified. However PDF, Jpeg, xlsx, .docs’ may contain programs, macros, or viruses that could potentially harm your computer.” This tricks the user to assume that the file in question has been verified and is safe to open. Once opened, the Word document triggers a download of an object with a hidden link. This object exploits a known vulnerability in Windows to steal the user’s key strokes.
The Challenges:
• There are more than 180K vulnerabilities in the digital world. Each of them can be exploited by hackers in various ways, in this case a sneakily crafted file name used to gain the trust of the user.
• The actual malware is delivered not by an intrusion attack but by an internal user’s web request when the Word document is opened, thus bypassing firewalls and IPS perimeter defenses.
• Many such attacks are successful by mutating known malware to evade signature based defense systems.
User credentials and private data can easily be assembled from logged keystrokes. This is compromising for businesses as everything from online banking access to social security numbers are entered into their computers. Cyber criminals can gather confidential information from business emails and messaging applications used to communicate between employees to further exploit companies with cyber ransoming.
The Solution:
Wedge Network’s malware lab tested a new Snake keylogger malware attack on a network protected by WedgeARP™. Zero Day attacks are difficult to detect and prevent because they employ never before seen malware. These new or mutated malware do not have a matching signature in the signature database and can easily slip into corporate networks to cause irreparable damage. To combat this, WedgeARP™ utilises Deep Learning Artificial Intelligence Anti Virus (AIAV) engine to identify and prevent Zero Day attacks. In the figure below, the new Snake keylogger is prevented from being downloaded by the user from a compromised file:
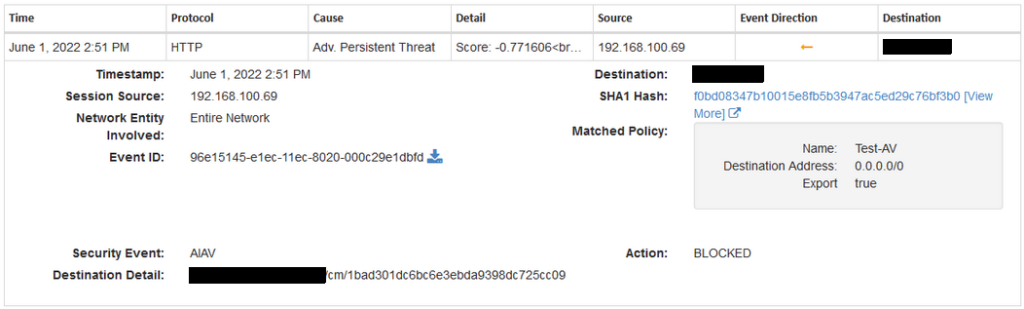
In Figure 1, the infected file on the device at 192.168.100.69 tries to download a Snake keylogger malware from an external server. Even though there are no identical signature of this new Snake keylogger malware, the malware was quickly detected, evaluated and dropped using AIAV engine. The engine determined that the never before seen Snake keylogger malware scored a malware value of -0.771606 and considered it malicious. The same result is replicated when using the advance Signature engines on the WedgeARP™, preventing the Snake keylogger malware from being downloaded by the device at 192.168.100.69 as seen below:
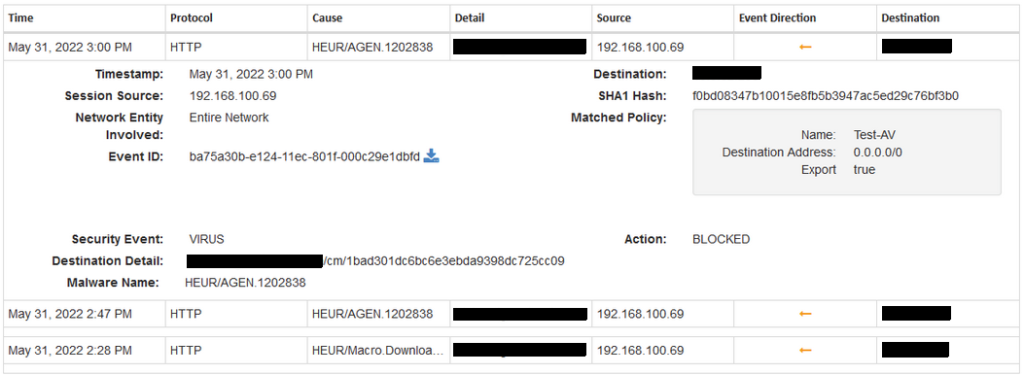
In both examples, WedgeARP™ prevents crippling Zero Day attacks from a new Snake keylogger malware using advanced AIAV and Signature engines. WedgeARP™ is a network based solution, meaning all devices from servers and work/personal computers to mobile and IOT electronics are protected from these clever and often devastating exploits.
With Wedge Real-Time Threat Prevention’s innovative Deep Content Inspection and highly trained Deep Learning AI engines, WedgeARP™ can identify and prevent these sneakily crafted malware from entering and compromising your business from within your corporate networks. If you are interested in our Real-Time Prevention Technology, feel free to contact our team at: info@wedgenetworks.com


