Lunch two Thursdays ago was a unique experience. We got to meet and present to Calgary‘s SPIE – a special interest group made up of the who-is-who in Calgary’s Internet Security Profession. Calgary, Canada’s Oil Capital, and without a doubt, companies in this sector fare the toughest – from hacktivism to pure evil crime with financial and business motives.
We discussed several topics (Presentation can be found here), but the most important points were:
- Rules of the Malware game have changed, from a focus 0n generating publicity to a multi-billion dollar industry funded by very organized and savvy criminals (you can read more about the malware industry’s business model here). And yes, they do have websites that sell botnets and that do provide support too!
To this end, malware being written these days are designed to “hide” in compromised systems so that hackers can continue to use the computers’ resources for criminal activity while remaining undetected as long as possible.
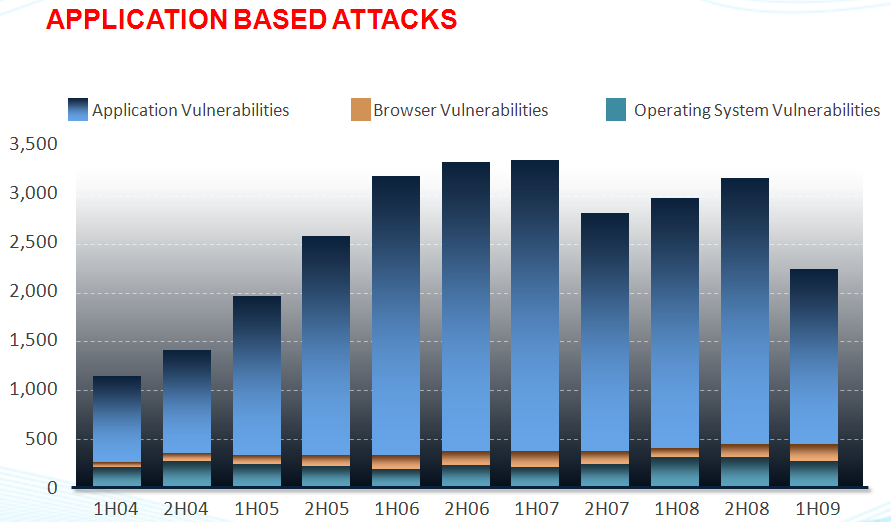
- Newest attack vector is Application Vulnerabilities, and even more so web-applications, as shown in the diagram. Notice that Operating System/Browser Vulnerabilties are now taking a back seat, with Application (e.g., Adobe Reader) vulnerabilities becoming the vector of choice for malware writers.
- Deep Content Inspection is the logical choice for combating this evolving threat- it is no longer sufficient to scan some packets against a limited set of viruses and to believe that is good enough. I will address this in next week’s blog.
- Layered approach to security is needed with network security being a lifecycle, and not a process.
I found this seminar to be very, very beneficial. Thanks to security vendors, CIOs are now marketing-shielded (yes, you heard it here first!). When the rubber hits the road, network security is accuracy and without performance compromise. It is good to break bread with SPIEs, ISSAs, etc.



Nice post ! Thank you for, writing on this blog page mate! I’ll email you some time.