Overview of Rootkits:
History: The first known rootkit was developed by John Lions as part of his commentary on the Unix source code in 1976. Lions’ Commentary on Unix 6th Edition, with Source Code, included a hidden backdoor that allowed privileged access to the system. This backdoor was intentionally added by Lions to demonstrate the importance of reviewing and understanding system code. It was not malicious but served as an educational tool.
Since then, rootkits have been a part of computer security concerns, with their name originating from the combination of “root,” denoting privileged access on Unix and Unix-like systems, and “kit,” referring to the software tools that grant such access. Initially, rootkits were simple modifications to system software that allowed unauthorized users to maintain access to a system while hiding their presence. Over the years, rootkits have evolved from simple command and control modifications to sophisticated programs that can intercept and modify standard operating system processes.
How Rootkits Work: Rootkits work by inserting themselves into or associating themselves with the operating system’s core functionalities, often at the kernel level, though user-mode rootkits also exist. By doing so, they can intercept system calls, hide certain processes, files, network connections, or registry entries, and avoid detection by system monitoring tools. Their primary purpose is to conceal malicious activities and maintain persistent, unauthorized access to a system.
Rootkits are adept at leveraging a variety of infiltration tactics to compromise systems, and they often do so through seemingly benign interactions. Here are some of the primary methods through which rootkits are known to spread, each illustrated with a notable example:
- Phishing Email Campaigns: A classic vector for rootkit distribution is phishing emails, which may appear as legitimate communications from trusted entities. For instance, the “Pretender” campaign targeted individuals with emails purporting to be job offers. These emails contained attachments that, once opened, would execute a rootkit, granting attackers deep system access.
- Malicious Executable Files: Rootkits often piggyback on executable files masquerading as genuine applications. The notorious “RegretLocker” rootkit, for example, was distributed through software cracks and keygens. Users downloading and executing these files inadvertently installed a rootkit capable of encrypting files and demanding ransom.
- Infected Documents: Documents can serve as trojan horses for rootkit delivery. A well-documented case is the “DoubleFantasy” exploit, where documents, when opened, would leverage vulnerabilities to install a rootkit that could steal information and open backdoors for future attacks. This technique often exploits macros or embedded scripts within PDFs or Microsoft Office documents to execute the malicious payload.
The sophistication of rootkits has evolved significantly:
- Early Rootkits: The first rootkits were relatively simple and involved modifying system binaries to conceal their presence. An early example is the 1987’s SunOS rootkit, which replaced critical system tools like ‘ps’, ‘netstat’, and ‘login’ to hide evidence of an attacker’s activity. This rootkit allowed attackers to maintain backdoor access to the system while remaining undetected by the system’s legitimate users.
- Kernel-Mode Rootkits: As operating systems became more complex and secure, attackers moved to kernel-mode rootkits that exploit vulnerabilities within the operating system’s kernel. A notable example is the 2005 Sony BMG copy protection rootkit, which was secretly installed on millions of CDs. It used kernel-mode techniques to hide the copy protection software and prevent copying of the CD, but also exposed users to significant security vulnerabilities.
- Bootkit is a variant of rootkits that infects the system’s bootloader, enabling it to load before the operating system and modify system behavior from the outset. One such example is the 2008’s ‘Mebroot’, target the system’s Master Boot Record (MBR), which is the first sector of the computer’s hard drive that the BIOS starts up. Mebroot would infect the MBR and load itself into memory before the operating system, giving it control over the boot process and allowing it to hide its presence and any payload it delivers.
- Firmware Rootkits represent an even more sophisticated threat, embedding themselves in hardware devices’ firmware, making detection and removal extremely challenging without specialized tools. An illustrative case is ‘LoJax’, discovered in 2018, the first documented UEFI rootkit used in the wild. LoJax targeted the UEFI, a modern replacement for the BIOS, and could persist on the motherboard’s flash memory, surviving disk replacements and system reinstallation. This article describes an advanced version of this rootkit. In 2022, Researchers discovered a malicious UEFI- based rootkit known as CosmicStrand. It has been active in the wild since 2016, ensuring that infected computers remain compromised even if an operating system is reinstalled or a hard drive is completely replaced. The firmware compromises the UEFI (Unified Extensible Firmware Interface), which is essential for booting up nearly every modern computer. CosmicStrand’s sophistication challenges the assumption that such UEFI malware is rare.
For advanced rootkits such as CosmicStrand, the only effective way to remove them is to reflash the firmware from hardware manufactures. In the case of CosmicStrand, this involves updating the firmware stored in its dedicated SPI flash memory chip. This process can be complex and risky, you may need to consult your motherboard manufacturer’s instructions or seek professional assistance. Last week, Wedge Networks’ security partners in Asia alerted us on a headline grabbing rootkit attack. On February 6, 2024, the hacker group R00TK1T targeted Maxis—a prominent telecommunications company in Malaysia.
Their initial breach targeted Maxis’ employee dashboards, exposing vulnerabilities. Subsequently, they bypassed Maxis’ firewall, infiltrating the telecommunications infrastructure of Maxis. Screenshots indicated R00TK1T demanded acknowledgment of their success, threatening to expose sensitive data unless Maxis complied. Other online articles such as “Maxis investigates cyberattack, suspects incident involved third-party vendor” and this article indicating R00TK1T had victims in many countries.
Real-time Prevention of The Rooting:
The advent of sophisticated rootkits, such as CosmicStrand and hacker groups such as R00TK1T, underscores the critical need for robust, real-time threat prevention mechanisms. Traditional methods of detection and remediation often fall short, particularly when faced with advanced rootkits capable of embedding themselves deep within system infrastructures. This reality propels real-time prevention to the forefront of cybersecurity strategies, emphasizing its indispensability in neutralizing threats before they manifest.
Best Practices for Comprehensive Real-time Threat Prevention:
A multi-faceted approach to network security, incorporating cutting-edge technologies and methodologies, is essential to effectively combat modern cyber threats:
- Intrusion Prevention Systems (IPS): Serving as the initial barrier against potential threats, IPS is instrumental in identifying and thwarting attempts to exploit vulnerabilities, often the primary ingress points for rootkits. Through continuous analysis of network traffic against known attack signatures and anomalous patterns, IPS ensures prompt action to secure the network’s perimeter.
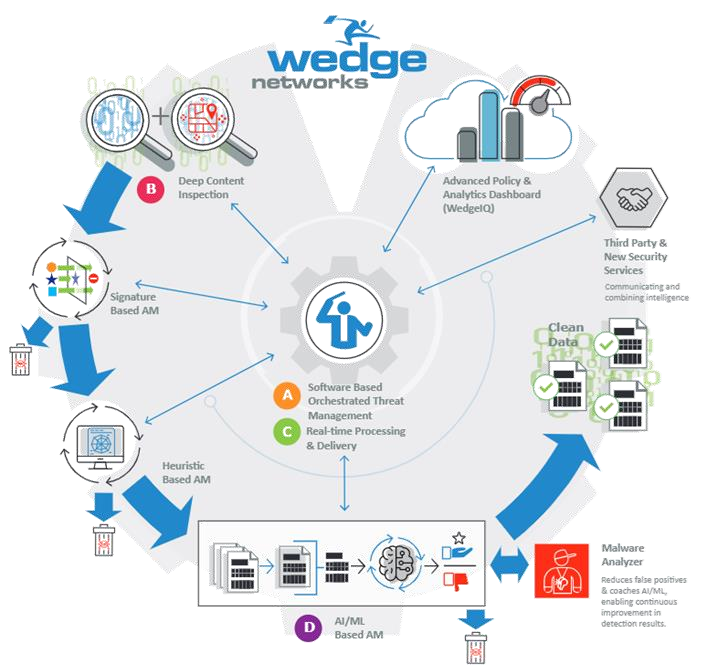
- Deep Content Inspection with TLS Interception: To counteract malware hidden within encrypted traffic, deep content inspection, augmented by TLS interception, is vital. This technique involves temporarily decrypting TLS-encrypted traffic to examine its contents for malicious code, then re- encrypting it before sending it to its destination. This process ensures that even communications believed to be secure are scrutinized, leaving no stone unturned in the search for hidden malware, including elusive rootkits.
- Web/DNS Filtering: By restricting access to malicious domains and websites known for distributing malware, Web/DNS filtering acts as a preventative measure against the download and proliferation of rootkits. This layer of defense is crucial in maintaining the integrity of network traffic and preventing users from inadvertently exposing the network to cyber threats.
- Zero Trust Edge Network Management:
- Network Access Control (Zero Trust on Device): Implementing a zero-trust framework ensures that no device is trusted by default, regardless of its location or previous interactions with the network. Each device must verify its identity and integrity to gain access, significantly reducing the attack surface.
- Content Filtering (Zero Trust on Content): This aspect of zero trust scrutinizes the content itself, applying stringent filters to all data entering or leaving the network, ensuring that only legitimate, safe content is allowed.
- Edge XDR for Suspicious Signal Detection and Real-time Isolation (Zero Trust on Status Quo): Extended Detection and Response (XDR) at the network edge enhances the ability to detect anomalous behaviors or signals indicative of a compromise. By maintaining a zero-trust stance on the status quo, edge XDR enables the real-time isolation of potentially compromised segments or devices, preventing the spread of threats within the network.
WedgeARP : A Synthesis of Best Practices:
WedgeARP epitomizes the integration and orchestration of these essential best practices into a singular, purpose-built high performance network security platform. Designed for ease of deployment and management, WedgeARP consolidates advanced IPS, TLS-intercepted deep content inspection, Web/DNS filtering, and zero-trust edge network management into a comprehensive solution. This not only facilitates the adoption of industry-leading security measures but also amplifies their effectiveness, providing businesses with a robust defense mechanism against the spectrum of cyber threats.
Since the beginning of 2024, the team at Wedge has been collaborating with our partners to share the latest advancements in cybersecurity technology through our exclusive product technology briefings. These sessions are crucial for understanding how cybersecurity solutions can be tailored to meet evolving security challenges. If you are concerned about rootkit attacks, please reach out to Wedge partners in your region. If you are not yet a partner but are eager to learn how Wedge can assist in enhancing your capability to safeguard your customers against rootkit attacks, we encourage you to get in touch. Send your inquiries to info@wedgenetworks.com, and our team will be pleased to demonstrate how our technologies can become an integral part of your security strategy. Together, let’s make our digital world safe and secure.
Contact us for more information